DDoS protection
360-degree L3, L4, and L7 DDoS protection
Keep websites, applications, and networks safe from L3, L4, and L7 attacks. Add an extra layer of protection and prevent attackers from targeting your origin server directly.
What is Mlytics DDoS Protection
Mlytics’s high-bandwidth, global Multi CDN network combines 2,300+ PoPs with 2,600 Tbps capacity from all of our CDN partners to absorb even the largest DDoS attacks.
Additionally, the platform also adds an extra layer of always-on L7 protection to keep mission-critical services safe from rogue crawlers, bad bots, and more.
Low effort
Available upon Multi CDN activation with zero configurations required.
Unmetered
Stops illegitimate volumetric traffic via multiple selected CDN edges without throttle.
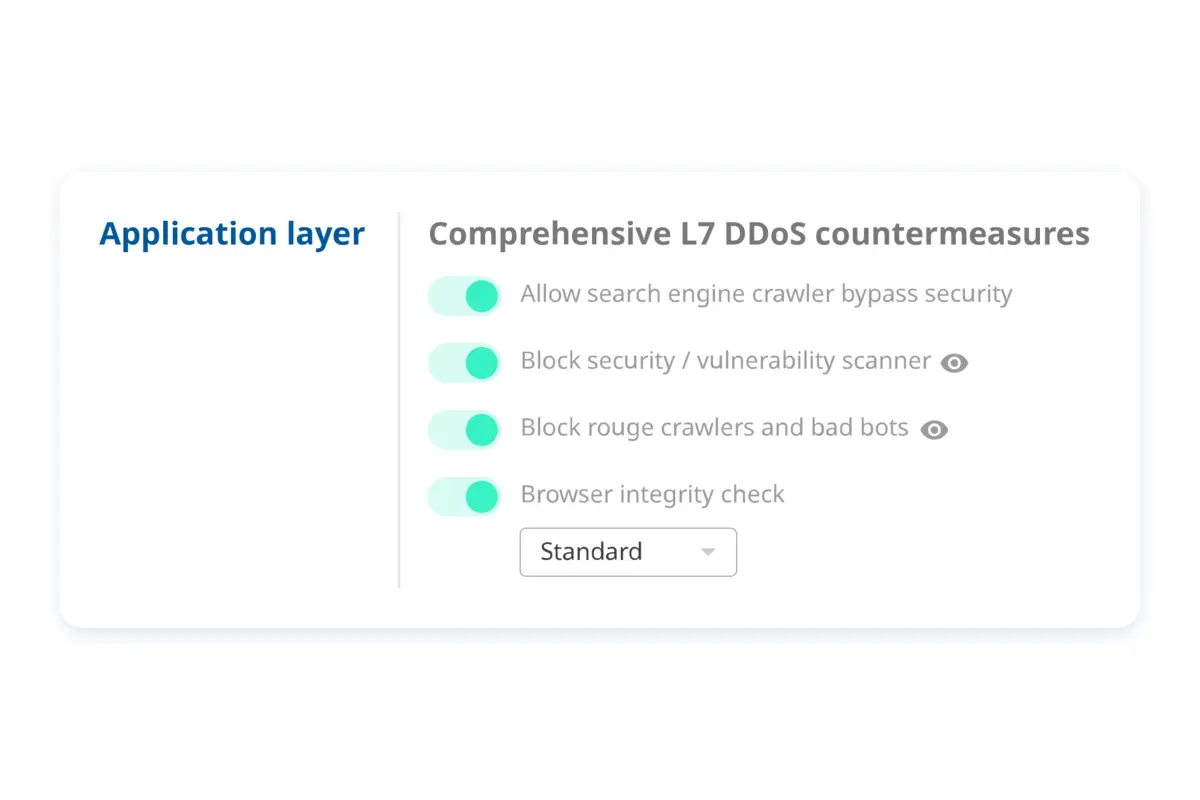
Comprehensive
L7 protection against bad bots, rogue crawlers, and other vulnerabilities.
Automatic filtering
Effortlessly filter out 90% of malicious requests
Inherent to CDN’s port protocol, Multi CDN automatically filters out all malicious requests targeting Layer 3 and 4 that aren’t accessing via port 80 and 443.
Always-on protection
Safeguard your website against even the largest attacks
Powered by a combination of 2,300+ PoPs and 2,600 Tbps capacity from all of our CDN partners, your website can sustain attacks via a multi-terabit-per-second globally distributed network.
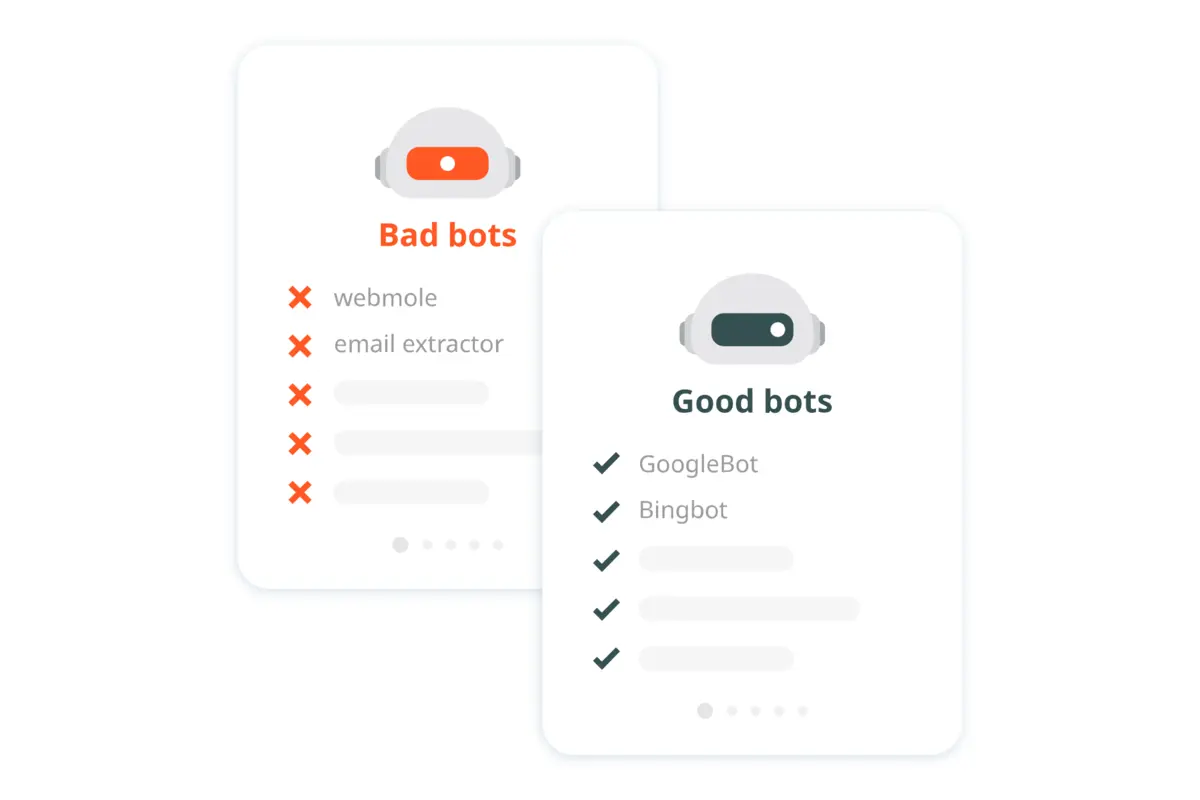
Bot management
Block the bad, let in the good
Good bots including GoogleBot, Bingbot, etc. are essential for your SEO ranking, and therefore should be let in. The system effectively identifies good bots and allows them to reach your site while at the same time preventing malicious traffic.
Reliability
Maximum security without sacrificing performance
Direct your traffic through the Mlytics platform to add an extra layer of protection to your sites and applications, and maintain maximum performance as traffic is directed to the best performing CDN via smart load balancing.
Choice and control
Take full control over your origin security
Set your origin protection policy according to your business’s needs, you can flexibly define your security policy. Gain full control over bot management, vulnerability scanner, crawler block, and more.