What is a DDoS Attack?
DDoS, or Distributed Denial of Service, is a cyber attack that disrupts a network’s normal functioning. To understand DDoS, we start with DoS, which shuts down a system using a single device. In DDoS, multiple devices join forces in an attack.
Attackers infect computers with malware, creating a “botnet” of zombie devices. Using this botnet, they overload a target network by exploiting vulnerabilities, using fake addresses to deceive, overwhelming resources like memory and bandwidth, and spamming to disrupt normal operations.
There are four basic types of DDoS attacks.
Volume-based Attacks:
What it does: Flood the target with a huge amount of traffic to disrupt its normal functioning.
Examples: UDP Flood (overloads with certain types of data packets), ICMP Flood (overloads with control message packets).
1. Protocol-based Attacks:
What it does: Exploit vulnerabilities in network protocols to disrupt the target.
Examples: SYN/ACK Flood (exploits the way computers start communication), Ping of Death (sends oversized packets to cause system crashes) and DNS query flooding.
2. Application Layer Attacks:
What it does: Target the specific applications or services running on the server.
Examples: HTTP/HTTPS Flood (overwhelms a website with web page requests), Slowloris (exploits how web servers handle connections).
3. Volumetric Attacks:
What it does: Overwhelm the target with a large volume of traffic.
Examples: DNS Amplification (uses open DNS servers to flood the target), NTP Amplification (uses Network Time Protocol servers).
In simple terms, DDoS attacks aim to disrupt online services by flooding them with traffic or exploiting vulnerabilities. Each type of attack has its own method, but the goal is to make a website or service unavailable to its users.
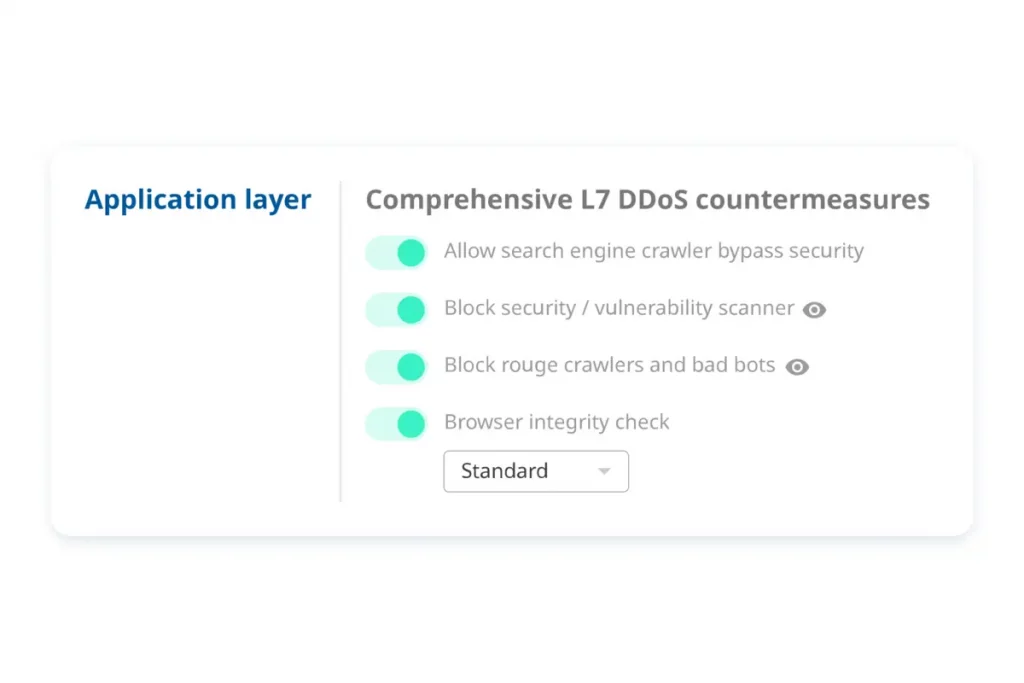
What is DDoS mitigation?
DDoS mitigation refers to the strategies and measures put in place to detect, prevent, and minimize the impact of DDoS attacks on a network, server, or online service – website and applications. The goal of DDoS mitigation is to ensure the availability and normal functioning of the targeted system, even in the face of a malicious flood of traffic.
Here are some common techniques and approaches used in DDoS mitigation:
DDoS mitigation methods
There are many DDoS mitigation methods, and each has its advocates. The three most common DDoS mitigation methods are Clean Pipe, CDN Attack Dilution, and Anti-DDoS Proxy.
The truth is, there’s no such thing as “the best mitigation method”, there’s only the most suitable method depending on different use cases. We’ll dive into each method mentioned above and help you understand and choose the best method for you.
Clean Pipe
Clean Pipe is one of the most common DDoS mitigation implementation methods of all three. To implement it, all incoming traffic must pass through a cleaning center also known as a “scrubbing center”, where malicious traffic is identified and separated, permitting only legitimate traffic to get to the server.
With the rise of DDoS attacks, many Internet Service Providers (ISPs) and Managed Security Service Providers (MSSPs) have begun to offer anti-DDoS services often referred to as “Clean Pipe”, where in the past, organizations were handling DDoS attacks with black-holing.
Clean Pipe is famous for its complexity of deployment. You need to have:
- BGP router
- A network device with the capability to terminate a GRE tunnel
- Internet routable prefixes and ASN
Constraints of Clean Pipe
- Detection and re-route lead time – Every time an attack on a customer is detected, re-routing techniques are needed to send the traffic to a center. This involves a detection diversion process that requires mitigation detection and takes at least several minutes from re-route to eventually mitigation kick-in which the enterprise online services are not protected and are exposed to the attackers.
- Incomplete mitigation and high false-positive – The Clean Pipe method does not provide complete protection against DDoS attacks. Firstly, they lack the capacity to handle just average size attacks, especially when it comes to packet-based / application flood attacks. Secondly, your IP prefix is not hidden. In contrast, an attacker can easily identify your infrastructure provider and exploit the loophole and weakness.
Besides, Clean Pipe re-route involves the entire prefix, typically it is at least /24. Under /24, computers with /24 might send traffic out as a client (for instance, query a DNS), and send traffic out as a server (for instance, serving web content). The mixing profile of the client and server-side traffic makes the mitigation profile very complex and introduces lots of false positives and therefore, you will find Clean Pipe often requires a lot of human intervention. - Mitigation Granular and Effectiveness – A cleaning center is designed to only drop malicious traffic but they cannot prevent an original attack. Security isn’t always a core capability of an ISP and they often don’t have the security expertise of a dedicated DDoS mitigation provider. As they are more focused on the volume of the attacks instead of focusing on signature and type of the attack. Hence leaving them vulnerable to the application layer/slow DDoS attacks.
High versatility is the key benefit of the Clean Pipe method, as it supports almost all applications in IP stack. But versatility has a tradeoff, it lacks advanced protection for a specific application, incurs high mitigation false-positives and high cost, which is critical for customers nowadays.
However, Clean Pipe is criticized because it’s coarse-grained. For instance, when trying to enable TCP RESET to counter TCP SYN Flood, some applications reconnect automatically without issue, but browsers may not be so lucky on the other hand.
CDN Dilution
Content delivery network (CDN) is a system of distributed servers (network) that deliver pages and other web content to a user. CDN is also known for its huge capacity in networking and the design of distribution of traffic. CDN Dilution is basically using geographically distributed servers to cache and deliver content, reducing the impact of DDoS attacks by distributing the load. It means using the huge bandwidth CDN technology is offering to mitigate to absorb L3/L4 DDoS attacks. We’ve covered more about how CDN (or specifically Multi CDN) can help you fight DDoS attacks effectively, read more here.
CDN can dilute DDoS attacks with its massive bandwidth like a whale。
CDN edge servers are working as reverse proxy for web applications. All requests will be handled by the edge server, and malicious requests will be filtered out before sending back to the origin. CDN Dilution offers the most comprehensive DDoS protection because:
- CDN edge servers are application context-aware
- A well-defined protocol (HTTP)
- It is always-on and no lead time
However, CDN Dilution only applies to web applications. If you are using a proprietary TCP/UDP application, then CDN Dilution won’t help.
Anti-DDoS Proxy
If you run TCP or UDP services on your origins such as web-servers, gaming services, remote server access (SSH), or email (SMTP), they are exposed through open ports. This means malicious attackers can send volumetric DDoS traffic or attempt to snoop sensitive, unencrypted data.
Some providers especially MSSP and CDN providers saw this demand and built a reversed TCP/UDP proxy in their existing DDoS infrastructure to offer an exact layer of protection to TCP/UDP application.
The Anti-DDoS Proxy works similarly to CDN. Packets are sent to reverse proxy and filter out malicious packets with a defined mitigation profile. Anti-DDoS Proxy offers an intermediate comprehensive level of DDoS protection with the following advantages:
- Always-On and no lead time
- A positive security model (allow defined port to access rather than open all)
- Able to fight against slow DDoS attack
A significant trade-off is that the source IP has changed for the backend. This may be a lethal issue to some of the applications given there is no way to get the real visitor’s IP.
Clean Pipe vs CDN Dilution vs Anti-DDoS Proxy
The differences between Clean Pipe, CDN Dilution, and Anti-DDoS Proxy (TCP/UDP Proxy) are huge. Though, they are not mutually exclusive and can supplement each other as a holistic solution. To simplify and conclude everything, here’s a comparison table to clear the air:
| CDN Dilution | Anti-DDoS Proxy | Clean Pipe | |
| Deployment mode | Reversed proxy | Proxy | Tunnel |
| Support application | Web application, static content, dynamic content, web socket | Any TCP or UDP application | Any application |
| Configuration | Per-domain basis | Per application basis | Per prefix basis |
| Deployment prerequisites | Internet | Internet | Support BGP Support TunnelRoutable /24 Prefix |
| Deployment lead time | Minutes | Minutes | Days |
| Origin load balancing | Support | Support | Not Support |
| L3/L4 DDoS protection | Yes, always ON | Yes, always ON | Yes but usually not always ON |
| False-positive | Low | Medium to Low | High |
| L7 mitigation capability | High | Medium/Low | Medium/Low |
| Others benefits | Content cache, web application firewall, application layer logging | Supports multiple ports on the same hostname or application, aka backend load balancing | Usually involves zero application changes |
| Constraints | Only applies to web application | Client IP will be replaced by proxy source-NAT IP. The origin server will not see the real IP anymore. | High false-positive and false-negative due to traffic profile mixed with client and server. |
What else you can do:
- Traffic Filtering:
- Rate Limiting: Restricting the rate of incoming traffic to manageable levels.
- IP Blacklisting/Whitelisting: Blocking or allowing traffic based on the source IP addresses.
- Signature-Based Filtering: Identifying and blocking known attack patterns.
- Anomaly Detection:
- Behavioral Analysis: Monitoring normal patterns of traffic behavior and identifying deviations that may indicate an attack.
- Heuristic-Based Analysis: Using algorithms to detect abnormal patterns that could be indicative of an ongoing DDoS attack.
- Traffic Scrubbing:
- Diverting incoming traffic through specialized DDoS mitigation services that filter out malicious traffic while allowing legitimate traffic to reach the target.
- Load Balancing:
- Distributing incoming traffic across multiple servers to ensure that no single server becomes overwhelmed.
- Web Application Firewalls (WAF):
- Implementing firewalls specifically designed to protect web applications by filtering and monitoring HTTP traffic.
- Incident Response Plans:
- Having a well-defined plan in place to respond quickly and effectively to a DDoS attack, including communication strategies, coordination with service providers, and steps to restore normal operations.
- Network Security Best Practices:
- Regularly updating and patching systems to address known vulnerabilities.
- Employing strong authentication mechanisms.
- Implementing access controls to limit unauthorized access.
Where to start
There are many ways to implement DDoS mitigation strategies, but oftentimes it’s difficult to create everything from scratch. As mentioned in this article:
It may seem unfortunate to have to pay to be properly protected against DDoS attacks, but remaining unprotected puts companies at great risk in terms of potential damages, time lost, and diminished customer trust.
It’s hard to avoid spending money on DDoS mitigation services nowadays even for small/mid businesses. But what we can do is find a way to put these investments to work when no attack is happening. Most DDoS mitigation services charge businesses money regardless of whether an attack is happening or not, except the DDoS mitigation service that uses CDN Dilution method.
Since the CDN Dilution method is built on CDN technology, businesses can still utilize the CDN to deliver their web assets during a peaceful period; when an attack occurs, the CDN can be used to dilute DDoS attacks . The Mlytics Enhanced Security feature is built based on this philosophy, which uses Multi CDN to absorb massive DDoS attacks and boost website performance.
Mlytics DDoS protection (powered by Multi CDN) for the network layer (L3/L4) is available under Pro plan; protection for the application layer (L7) is available under Business plan.
You can also rely on experts in dealing with DDoS attacks and security – Mlytics SOC (Security Operations Center) – our team of guardians, committed to securing web and application digital presence. With a focus on ‘Your Security, Our Responsibility,’ Mlytics SOC brings together highly skilled cybersecurity professionals ready to safeguard your websites, applications, and online assets.
Why choose Enterprise support with Mlytics?

- 24/7 Vigilance and Expertise: Mlytics SOC’s enterprise support team operates around the clock, ensuring unwavering vigilance against potential threats. Comprising cybersecurity veterans, this team is equipped with the expertise to navigate the complexities of the digital landscape and protect your valuable assets from a myriad of cyber threats.
- DDoS Mitigation Squad: Consider Mlytics SOC as your own DDoS mitigation squad, ready to report for duty against the ever-looming threat of distributed denial-of-service (DDoS) attacks. The team’s determination and extensive experience empower them to navigate the chaotic internet world, shielding your website from disruptions.
- Tailored Security Solutions: Understanding that each business and industry faces unique challenges, the Mlytics SOC team conducts a comprehensive analysis of your security situation. The result is highly tailored security solutions designed to mitigate risks specific to your business, providing a customized defense strategy.
- Global Support for Your Web & App: Mlytics SOC offers 24×7 global support, ensuring that you receive near real-time assistance whenever and wherever you need it. This global presence allows you to focus on growing your business while trusting that the Mlytics SOC team is diligently working to secure your digital assets.
In the realm of cybersecurity, Mlytics SOC is not just a team; we are your dedicated partners in fortifying your digital defenses, allowing you to navigate the digital landscape with confidence and resilience.
Learn more on the pricing page.