In the first quarter of 2019, one of our customers came to us with a problem: their website was under attack.
No matter what they tried to get around the problem, their site kept crashing. The kind of attack being used on this particular client is known as a distributed denial of service (DDoS) attack, specifically a challenge collapsar (CC) attack.
In this case study, we’ll go into what a DDoS attack is in more detail, define the specific type of DDoS attack being sued here (CC attack) and explain how we were able to help our client mitigate the problem.
What is a CC attack?
There are many types of DDoS attacks in the wild, and a CC attack is classified as a DDoS application layer attack. When a CC attack occurs, multiple HTTP requests are sent simultaneously to overload the server, since the Uniform Resource Identifiers (URIs) has to undertake complicated algorithms or database operations to exhaust the resources of the targeted web server.

Imagine multiple missile trucks firing at your website
The attacker simulates a scenario where a large number of users are accessing pages all the time. Because the accessed pages require a lot of data operations (consuming many CPU resources), the CPU usage is kept at the 100% level until normal access requests are blocked.
See all types of DDoS attacks here.
Fun fact: CC attacks got the name “Challenge Collapsar” attacks in 2004 when a Chinese hacker who went by the monicker Kiki invented a hacking tool called Collapsar capable of blitzing a server with HTTP requests.
One of the largest CC (DDoS) attacks we’ve seen in a while
Our customer tried everything they could think of to mitigate the attack: they tried to solve the problem via in-house DDoS mitigation and used content delivery network (CDN) services and providers who claimed they could help mitigate DDoS attacks. But each attempt failed, and their site would go down after just a few minutes when relaunched.
When the customer came to us to help solve their problem, we immediately took action to mitigate the attack. Upon investigation, we were surprised at the massive scale of this DDoS attack: 300 million requests were being sent to our customer’s server every minute, and the hacker was utilizing “user mimicking,” a practice which masks the attack traffic as normal user traffic distributed across multiple IP addresses.
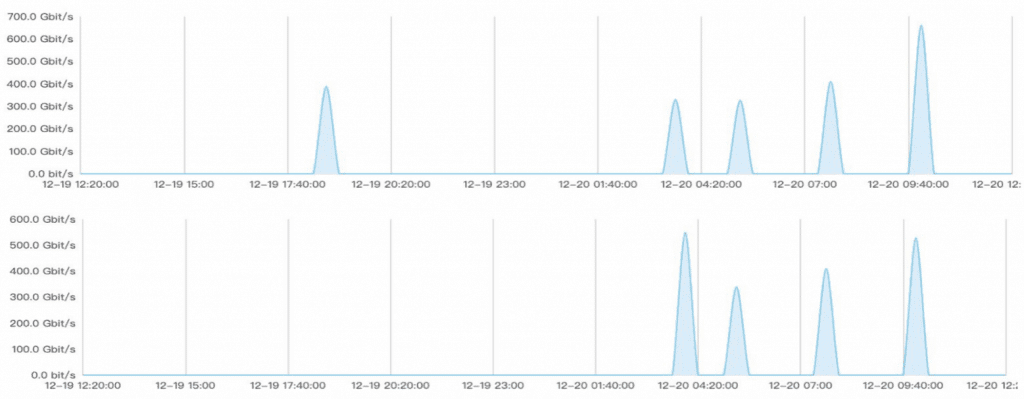
Approximately 1.3 Tbps of network attack
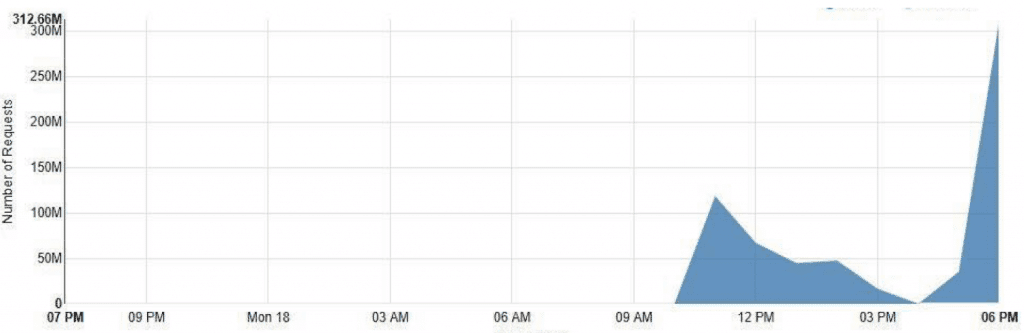
Approximately 300M QPM of application attack
We were able to mitigate the attack and get our customer’s site up and running again, even during such a brute-force CC attack.
How we mitigated the attack
We used a two-pronged method of DDoS protection to mitigate this particular CC attack:
- Geo-restriction: We were able to restrict incoming traffic to specific regions by securing traffic from the main user base’s countries and regions, as well as preventing incoming traffic from known “attack regions” like Russia, Ukraine, and India.
- Enabling browser-based challenge: Our web application firewall (WAF) lets us use challenge-based algorithms to filter out CC attack bots. Built on global public cloud infrastructure, we can leverage that computing power via Multi CDN to autoscale our defenses proportionate to the attack. It’s that power that let us fend off a 300-million request per minute CC attack.
In order to implement this strategy, we needed a solid, powerful infrastructure. Mlytics uses Multi CDN which combine the power of over 2,300 PoPs to give us a 2,600 Tbps capacity. That gives us a global network with the power of multi terabit-per-second capacity with which to fend off DDoS attacks.
By combining effective filtering with the power of our network, we were able to help our customer absorb even that powerful CC attack and get their site back up and running.



